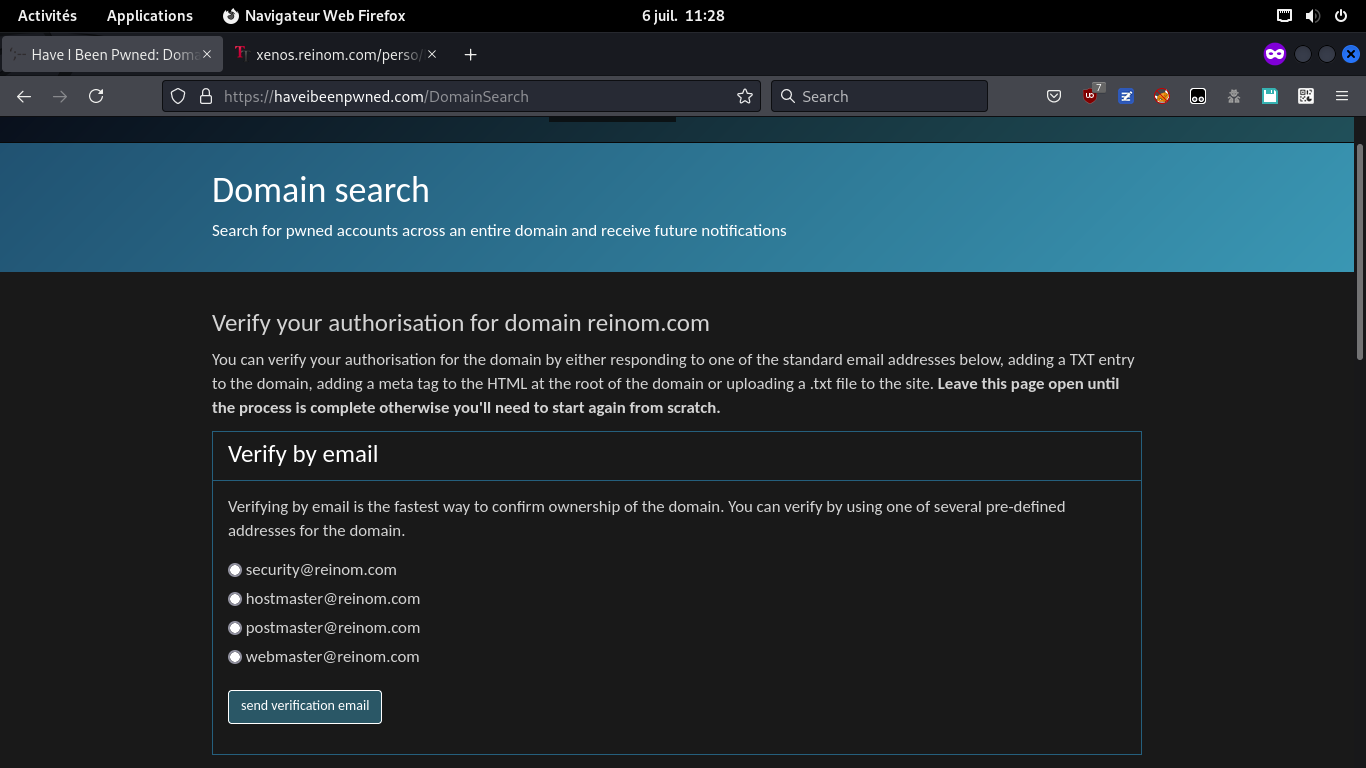
OSINT from HaveIBeenPwned
If a domain allows to create email redirections or mail boxes, create one of the domain-validation emails for HaveIBeenPwned (ie: security@ webmaster@ hostmaster@ postmaster@) and look for all pwned emails for this domain.
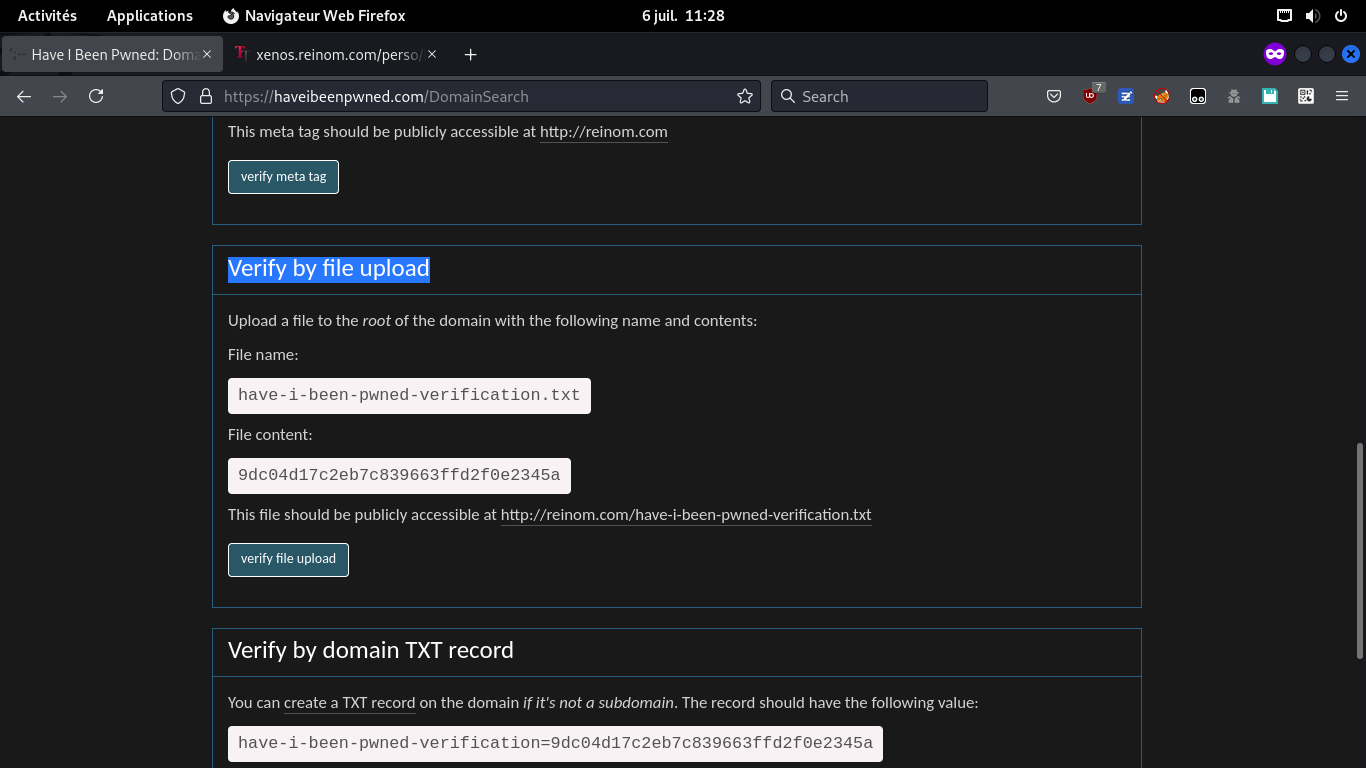
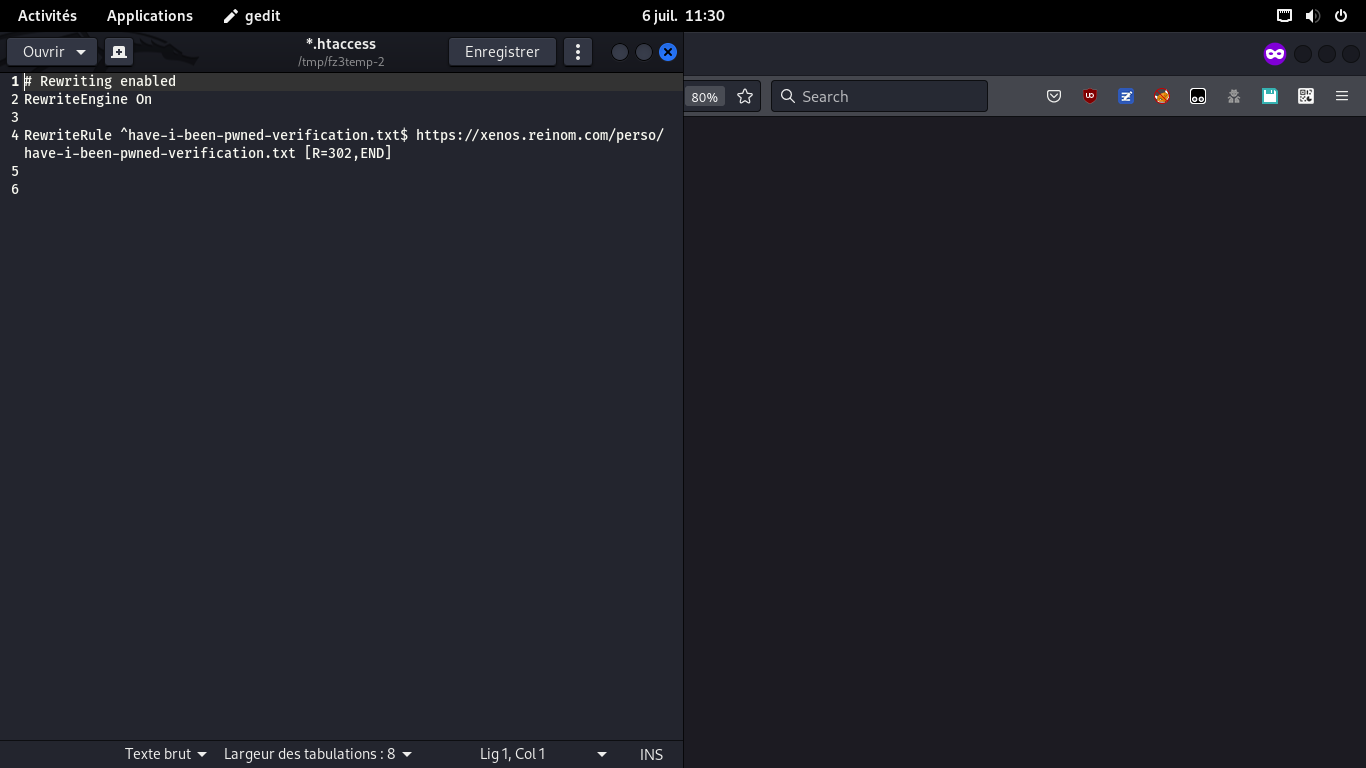
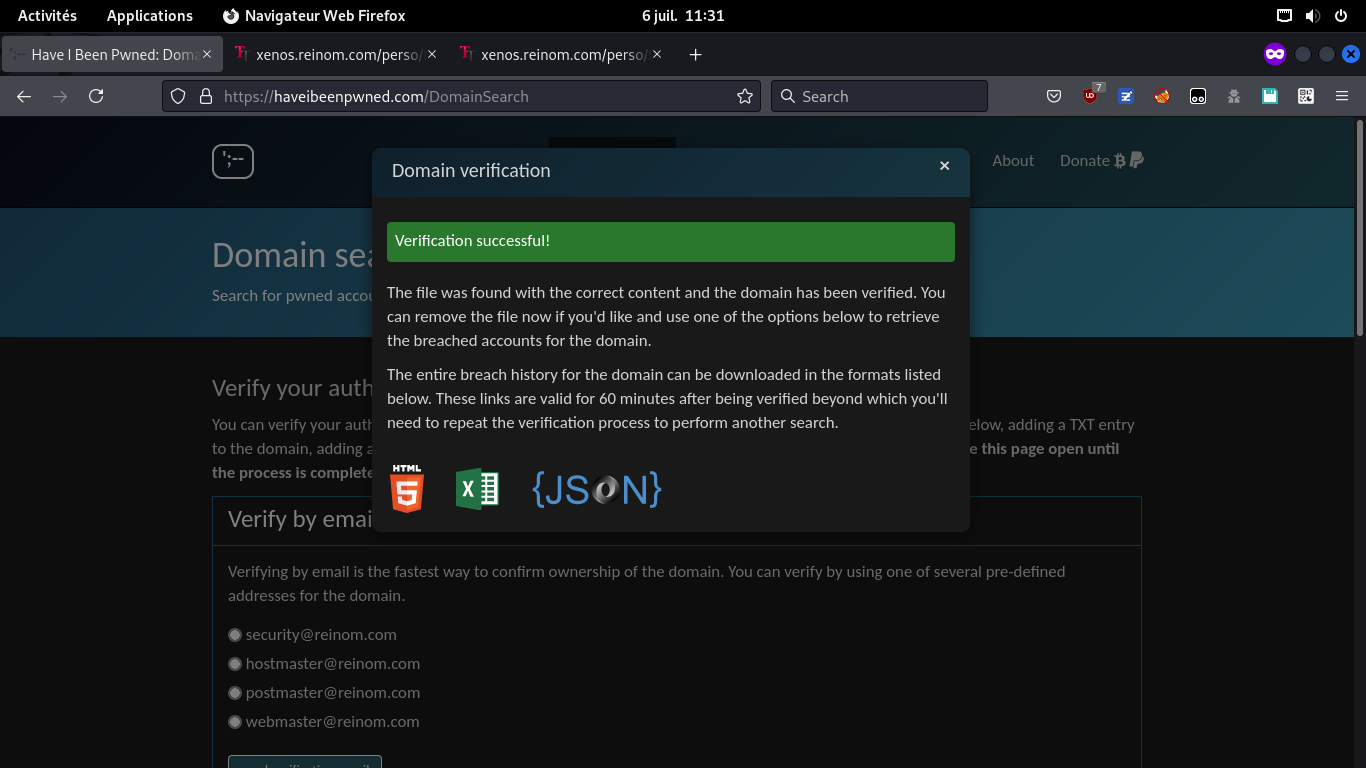
Same if website allows file upload to root, or redirections from root with arbitrary path (good for any short-linker!). Example: https://…/
Apache-known extensions
When web application allows for file upload, look for "rare" extensions
that might not have been blacklisted.
Examples: phtml, xht, svgz, rss,
…
This text file
contains all extensions that my Apache setup recognized, and
here is a ZIP file
containing scripts to generate and test such list.
Properly prepare the report
Log commands
Always use | tee … to keep track of you command results,
or use script -fB pentest.log to record all inputs and outputs.
Take screenshots
Take regular screenshots during labs/CTF/assessment, so it can be directly used in the report. Don't worry: all screens won't be useful, but you never know which ones will!
Escalate reverse-shell
TTY/PTY spawn
Pwncat-cs
pwncat-cs:
pip3 install pwncat-cs or
python3 -m pip install pwncat-cs and run
python3 -m pwncat :8080
See
Vulnversity lessons learned
Searchsploit
searchsploit -x {{exploit ID 50512 or path or whatever}} for examining the exploit
searchsploit -m {{ID;path;etc}} for copying the exploit to current directory
python3 $(locate exploit_file.name) args args for running the exploit (or cat $(locate exploit.py), etc)